
Alarming Trend: 159 Vulnerabilities Exploited in Q1 2025 with Over 28% Weaponized Within 24 Hours
The Vulnerability Race – Vulnerabilities Exploited with 28% Weaponized in 24 Hours
Alarming Trend: 159 Vulnerabilities Exploited in Q1 2025 with Over 28% Weaponized Within 24 Hours
Staying ahead of threat actors requires constant vigilance and awareness of emerging exploitation trends. The recently released VulnCheck Q1 2025 report reveals concerning patterns that all businesses, especially small and medium-sized organizations, need to understand to protect their digital assets.
 Key Findings from the VulnCheck Q1 2025 Report
Key Findings from the VulnCheck Q1 2025 Report
VulnCheck identified evidence of 159 CVEs (Common Vulnerabilities and Exposures) that were publicly disclosed for the first time as exploited in the wild during Q1 2025. This represents an increase from 151 vulnerabilities in Q4 2024, highlighting the relentless pace at which new security flaws are being discovered and weaponized.
Perhaps most concerning is the speed at which attackers are exploiting these vulnerabilities. 28.3% of vulnerabilities were exploited within just 24 hours of their CVE disclosure. This translates to 45 security flaws that were weaponized in real-world attacks within a single day of becoming public knowledge. This trend continues from a similar pace observed in 2024, demonstrating that threat actors are becoming increasingly efficient at operationalizing new exploits.
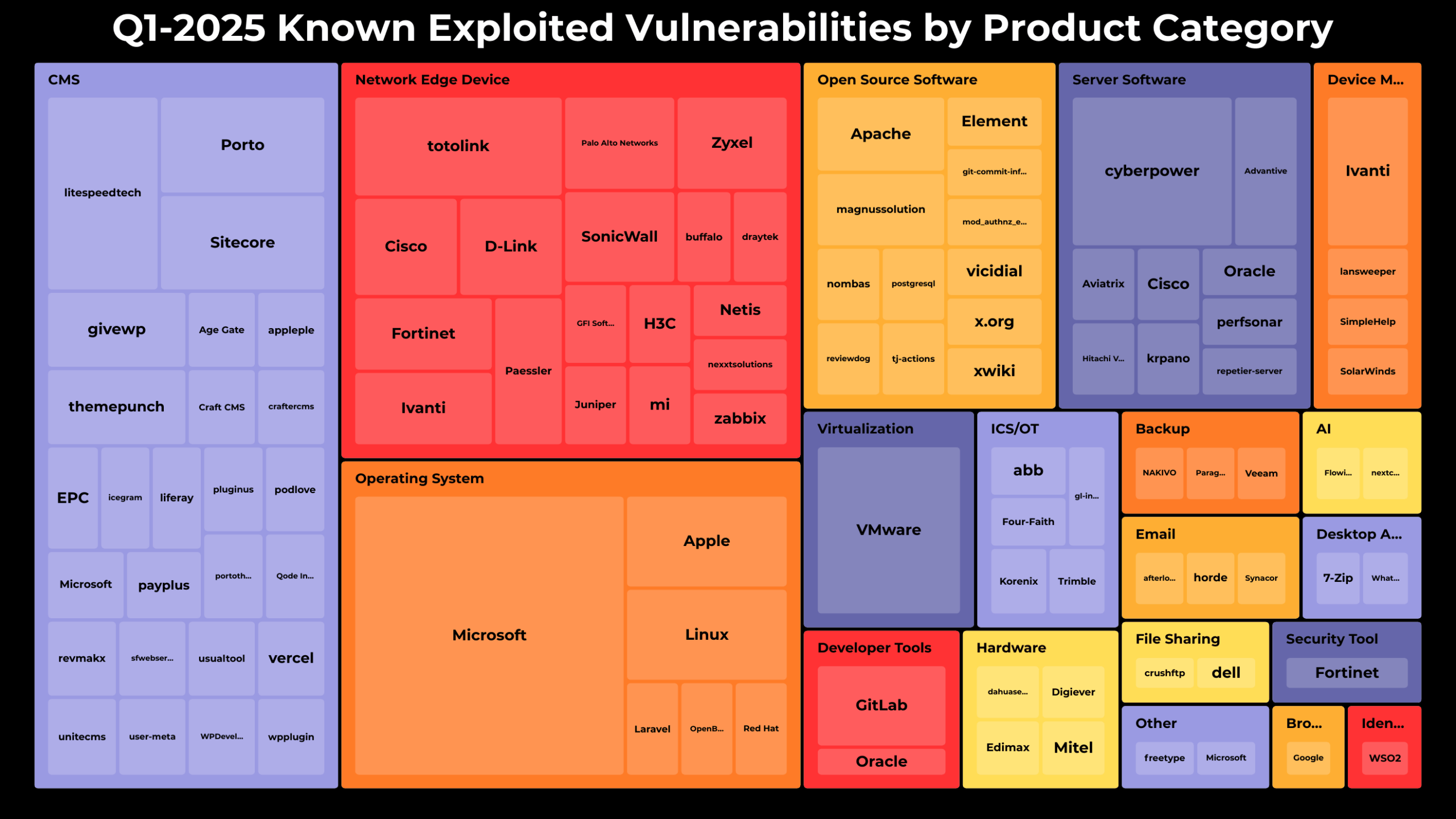
The report provides valuable insights into which systems are most frequently targeted:
The top five categories associated with exploited vulnerabilities were:
- Content Management Systems (CMS): 35 vulnerabilities
- Network Edge Devices: 29 vulnerabilities
- Operating Systems: 24 vulnerabilities
- Open Source Software: 14 vulnerabilities
- Server Software: 14 vulnerabilities
The leading vendors and products affected by these exploits included:
- Microsoft Windows: 15 vulnerabilities
- Broadcom VMware: 6 vulnerabilities
- Cyber PowerPanel: 5 vulnerabilities
- Litespeed Technologies: 4 vulnerabilities
- TOTOLINK Routers: 4 vulnerabilities
 Concerning Trends for Defenders
Concerning Trends for Defenders
Several trends in the report should raise alarm bells for security professionals:
- The pace of exploitation appears to be marginally faster than what was observed in 2024, indicating that threat actors continue to move quickly on new vulnerabilities.
- While the year started slowly (likely a seasonal pattern), there was a surge toward the latter half of the quarter in public exploitation disclosures. On average, 11.4 vulnerabilities were disclosed weekly, and 53 per month.
- While CISA’s Known Exploited Vulnerabilities (KEV) catalog added 80 vulnerabilities during the quarter, only 12 showed no prior public evidence of exploitation. This suggests that many vulnerabilities are being actively exploited before they appear on official watchlists.
- According to Verizon’s newly released Data Breach Investigations Report for 2025, exploitation of vulnerabilities as an initial access step for data breaches grew by 34%, accounting for 20% of all intrusions.
- Data from Google-owned Mandiant revealed that exploits were the most frequently observed initial infection vector for the fifth consecutive year, with stolen credentials overtaking phishing as the second most frequently observed initial access vector.
- Analysis of vulnerability scoring systems showed that only a handful of vulnerabilities had elevated EPSS (Exploit Prediction Scoring System) scores on the same day as exploitation disclosure, despite being known to have been exploited. This suggests that EPSS is largely a trailing indicator rather than a predictive tool for emerging threats.
- Of the 159 vulnerabilities with known exploitation, 25.8% are still awaiting or undergoing analysis by NIST’s National Vulnerability Database, and 3.1% have been assigned the new “Deferred” status. This lag in official analysis could leave organizations vulnerable if they rely solely on these sources.
 Implications for Your Business
Implications for Your Business
The findings from this report have several critical implications for businesses of all sizes:
- The vulnerability gap is widening: With over a quarter of vulnerabilities being exploited within 24 hours of disclosure, traditional patch management cycles that take days or weeks leave organizations exposed during the most critical period.
- Internet-facing systems remain primary targets: Content Management Systems and Network Edge Devices top the list of exploited categories, emphasizing the need for enhanced security for internet-facing assets.
- Popular software remains in the crosshairs: Microsoft Windows continues to be the most frequently exploited product, highlighting the importance of prompt patching for widely used systems.
- Traditional scoring systems may not be reliable for emerging threats: Relying solely on vulnerability scoring systems like CVSS or EPSS may not provide adequate protection against newly exploited vulnerabilities.
- Detection Capabilities: Despite attackers’ efforts to evade detection, the global median dwell time (the period from compromise to detection) was 11 days, an increase of just one day from 2023. This suggests that while threats are evolving, detection capabilities are largely keeping pace.
 How CinchOps Can Protect Your Business
How CinchOps Can Protect Your Business
In this evolving threat environment, businesses need a proactive cybersecurity partner that can respond quickly to emerging threats. Here’s how CinchOps can help secure your business:
- Rapid Vulnerability Assessment and Patching: Our expert team monitors emerging threats in real-time and implements critical patches within hours, not days or weeks, closing the vulnerability window that attackers exploit.
- Comprehensive System Hardening: We implement defense-in-depth strategies for your internet-facing systems
- 24/7 Threat Monitoring and Response: Our Security Operations Center continuously monitors your systems for signs of compromise, ensuring that even if an attack occurs, we can detect and respond to it quickly.
- Custom Security Policies: We develop tailored security policies based on your specific technology stack and risk profile, not one-size-fits-all approaches that leave gaps in your defense.
- Employee Security Training: We train your team to recognize and respond to security threats, creating a human firewall that complements your technical defenses.
- Regular Security Assessments: We conduct comprehensive security assessments to identify and address vulnerabilities before attackers can exploit them.
The VulnCheck Q1 2025 report makes one thing clear: the pace and sophistication of cyber threats con tinue to accelerate. For small and medium-sized businesses without dedicated security teams, partnering with a managed IT security provider like CinchOps isn’t just a good idea—it’s essential for survival in today’s digital environment.
Don’t wait until after a breach to take cybersecurity seriously. Contact CinchOps today to learn how we can help protect your business from the latest threats.
 Discover More
Discover More 
Discover more about our enterprise-grade and business protecting cybersecurity services: CinchOps Cybersecurity
Discover related topics: Patching Vulnerabilities Faster: The Key to Reducing Cyber Risk
For Additional Information on this topic: 2025 Q1 Trends in Vulnerability Exploitation
![]()
FREE CYBERSECURITY ASSESSMENT



