Win-DDoS Attack: How Cybercriminals Turn Your Domain Controllers Into DDoS Weapons
Win-DDoS Exploits LDAP Referrals To Turn Domain Controllers Into Unwitting DDoS Weapons – Practical Guidance For Implementing Microsoft Patches Against Win-DDoS Attack Vectors
Win-DDoS Attack: How Cybercriminals Turn Your Domain Controllers Into DDoS Weapons
![]()
TL;DR: New Win-DDoS vulnerabilities allow attackers to weaponize public domain controllers worldwide, creating massive botnets for distributed denial-of-service attacks without purchasing infrastructure or leaving traces on compromised systems.
![]()
A groundbreaking discovery by SafeBreach researchers has exposed a critical security flaw that transforms the very infrastructure businesses rely on into weapons against them. The Win-DDoS attack technique represents a paradigm shift in cybersecurity threats, where attackers can hijack thousands of public domain controllers worldwide to launch devastating distributed denial-of-service attacks without ever compromising a single machine.
This isn’t your typical cybersecurity vulnerability. Win-DDoS leverages fundamental flaws in how Windows handles LDAP referrals, turning the trusted communication protocols that keep businesses running into vectors for unprecedented attacks. For Houston businesses relying on managed IT support and network security, understanding this threat is crucial for maintaining operational resilience.
(DDoS Demo – Source: Safebreach)
 What is Win-DDoS?
What is Win-DDoS?
Win-DDoS represents a novel attack methodology that exploits inherent weaknesses in Windows domain controller architecture. Unlike traditional DDoS attacks that require attackers to build and maintain expensive botnet infrastructure, Win-DDoS allows cybercriminals to commandeer legitimate domain controllers across the globe, transforming them into unwitting participants in massive coordinated attacks.
The attack technique centers around manipulating the LDAP referral process – a legitimate feature that allows directory servers to redirect clients to other servers when they don’t have requested information. By sending specially crafted Remote Procedure Call (RPC) requests to internet-accessible domain controllers, attackers can force these critical systems to become LDAP clients that follow malicious referrals.
Here’s what makes Win-DDoS particularly dangerous:
- Scale and Power: Attackers can harness tens of thousands of domain controllers worldwide, creating botnets with massive bandwidth capabilities that dwarf traditional compromised device networks.
- Stealth Operations: No code execution or credentials are required, meaning attackers leave no forensic footprint on the hijacked domain controllers.
- Zero Infrastructure Cost: Unlike conventional DDoS operations that require purchasing or renting botnet services, Win-DDoS requires only a domain name and basic server setup.
- Global Reach: The attack can be executed from anywhere with internet access, targeting victims across different geographical regions while using domain controllers from various countries.
The sophistication of this attack represents a fundamental shift in how we must think about cybersecurity and managed IT support strategies. Traditional security models assume that internal systems are safe from abuse unless fully compromised – Win-DDoS shatters this assumption entirely.
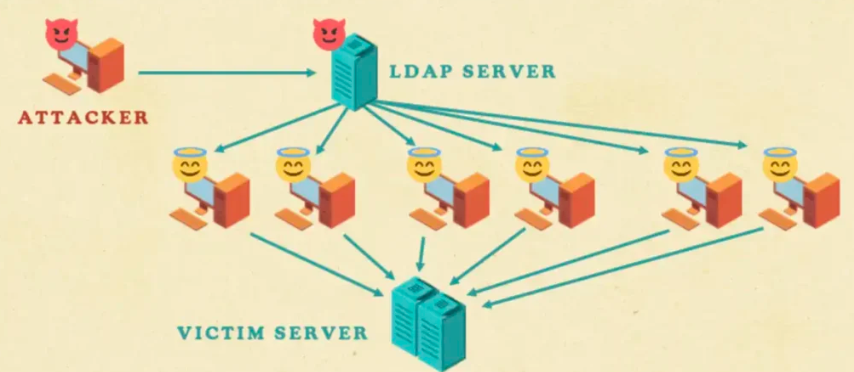
(The Win-DDoS Attack Technique – Source: Safebreach)
 The Technical Exploitation Process
The Technical Exploitation Process
The Win-DDoS attack unfolds through a carefully orchestrated sequence that exploits the trust relationships inherent in directory services. Understanding this process is essential for IT support teams managing network security for small businesses and enterprises alike. The attack leverages legitimate Windows protocols in ways that make detection extremely challenging while creating devastating impact for both hijacked systems and attack targets.
- Initial Compromise Phase: Attackers send specially crafted RPC calls to publicly accessible domain controllers, triggering them to become CLDAP clients that establish contact with malicious CLDAP servers while appearing completely legitimate to monitoring systems.
- Protocol Transition Exploitation: The attacker’s CLDAP server responds with referral information directing domain controllers to contact LDAP servers over TCP, removing UDP packet size limitations and enabling massive referral list transmission.
- Referral List Weaponization: Malicious LDAP servers respond with thousands of unique LDAP URLs that all resolve to the same victim IP address, bypassing Windows duplicate referral checks while overwhelming targets with connection requests.
- Memory Exhaustion Attacks: Referral lists consume substantial memory on domain controllers without release until processing completes, potentially causing LSASS crashes and system reboots independent of external targeting.
- Sustained Attack Persistence: Domain controllers continue processing referrals until entire lists are exhausted, ensuring prolonged attack duration that can overwhelm target defenses and exhaust network resources.
- Detection Evasion Mechanisms: The attack uses legitimate protocol behavior throughout the exploitation chain, making it extremely difficult for traditional network security appliances to identify malicious activity.
(Windows Domain Controller Crash – Source: Safebreach)
For managed services providers and cybersecurity professionals, this technical understanding highlights why traditional DDoS protection mechanisms may prove inadequate against Win-DDoS attacks that weaponize trusted infrastructure components.
 Threat Actors and Attack Motivation
Threat Actors and Attack Motivation
The Win-DDoS vulnerability creates opportunities for various threat actor categories, each with distinct motivations and capabilities that pose unique risks to organizations. Understanding these different groups helps Houston businesses and their managed IT support teams develop appropriate defensive strategies. The accessibility and power of Win-DDoS attacks fundamentally alter the cyberthreat environment by removing traditional barriers that previously limited large-scale attack capabilities.
- State-Sponsored Actors: Nation-state groups can leverage Win-DDoS for false flag operations, using domain controllers from one country to attack targets in another while providing plausible deniability for cyber warfare activities and potentially triggering international incidents.
- Ransomware Criminal Organizations: Cybercriminal groups focused on extortion find Win-DDoS attractive because it eliminates expensive botnet infrastructure costs while providing massive attack capabilities for demanding ransom payments to stop devastating assaults.
- Hacktivist Groups: Ideologically motivated activists benefit from Win-DDoS accessibility and global reach, allowing small groups with limited resources to execute attacks rivaling well-funded criminal enterprises for coordinating international campaigns.
- Lower-Tier Cybercriminals: The technique reduces technical expertise and financial resources required for large-scale attacks, potentially increasing the number of threat actors capable of significant damage to critical infrastructure and business operations.
- Opportunistic Attackers: Script kiddies and amateur hackers gain access to enterprise-level attack capabilities without requiring advanced technical skills or expensive infrastructure investments, democratizing high-impact cyber attacks.
- Corporate Espionage Groups: Industrial competitors and corporate spies can use Win-DDoS to disrupt business operations, damage reputation, or create cover for data theft operations while maintaining anonymity.
The convergence of these threat actor motivations with Win-DDoS capabilities creates a perfect storm for escalating cyber conflicts, where attribution becomes nearly impossible and the potential for collateral damage increases exponentially across interconnected business networks.
 Who is at Risk?
Who is at Risk?
The Win-DDoS vulnerability creates a complex risk environment where organizations face threats both as potential attack platforms and as potential victims. Understanding these dual risk factors is essential for small business IT support teams and managed services providers developing comprehensive protection strategies. The interconnected nature of modern business networks means that Win-DDoS risks extend far beyond traditional cybersecurity threat models.
- Internet-Accessible Domain Controllers: Organizations operating Windows domain controllers with internet accessibility face immediate risk of involuntary participation in attacks, including businesses exposing controllers for remote access, cloud-hosted Active Directory services, and misconfigured firewall environments.
- High-Value Target Industries: Financial institutions, healthcare providers, government agencies, and critical infrastructure operators are particularly attractive targets for attackers seeking maximum impact through Win-DDoS assaults on their public-facing services.
- Small and Medium-Sized Businesses: Companies with limited security resources, dependence on managed IT support near them, network infrastructure limitations, and restricted incident response capabilities face elevated vulnerability to both exploitation and targeting.
- Healthcare Organizations: Medical facilities dependent on electronic health records and telemedicine platforms face patient safety risks during sustained DDoS attacks that could disrupt critical care delivery systems and emergency response capabilities.
- Manufacturing Companies: Industrial organizations with internet-connected operational technology may experience production disruptions, supply chain interruptions, and safety system failures during Win-DDoS attacks targeting their control networks.
- Educational Institutions: Schools and universities could lose access to critical learning management systems, student services, and administrative functions, disrupting educational delivery and institutional operations.
- Geographic Risk Concentrations: Organizations in regions with large numbers of internet-accessible domain controllers may face higher attack volumes, while businesses in areas with limited cybersecurity infrastructure struggle with effective incident response.
The dual nature of Win-DDoS risks means that organizations must simultaneously protect against becoming unwitting attack participants while defending against incoming assaults, requiring comprehensive security strategies that address both internal infrastructure hardening and external threat mitigation.
 Remediation and Protection Strategies
Remediation and Protection Strategies
Defending against Win-DDoS attacks requires a multi-layered approach that addresses both the vulnerability exploitation mechanisms and the resulting DDoS impacts. Effective remediation strategies must consider both preventing organizational systems from being weaponized and protecting against incoming attacks. The complexity of Win-DDoS threats demands comprehensive security planning that goes beyond traditional patch management to encompass network architecture, monitoring capabilities, and incident response procedures.
- Emergency Patch Management: Immediate deployment of Microsoft security updates addressing CVE-2025-26673, CVE-2025-32724, CVE-2025-49716, and CVE-2025-49722, with prioritization for internet-facing domain controllers that could be exploited as attack platforms.
- Network Architecture Hardening: Evaluation of domain controller internet accessibility requirements, implementation of network segmentation to isolate critical directory services, and deployment of properly configured SD-WAN solutions for granular access control.
- Cloud-Based DDoS Protection: Implementation of cloud-based DDoS mitigation services capable of absorbing and filtering attack traffic before it reaches organizational networks, providing scalable protection against massive Win-DDoS assaults.
- Advanced Network Security Appliances: Deployment of enterprise-grade firewalls and intrusion prevention systems capable of identifying and blocking malicious LDAP traffic patterns while maintaining legitimate directory service functionality.
- Comprehensive Monitoring and Detection: Implementation of logging and alerting systems for unusual LDAP traffic patterns, unexpected external connections from domain controllers, and anomalous resource consumption indicating potential exploitation attempts.
- Incident Response Planning: Development of clear procedures for responding to DDoS attacks, including communication protocols, alternative operational methods, and coordination with managed services providers for rapid threat mitigation.
- Regular Security Assessments: Conducting periodic evaluations of domain controller configurations, internet exposure analysis, and vulnerability testing to identify potential Win-DDoS attack vectors before they can be exploited.
The interconnected nature of Win-DDoS threats means that effective protection requires coordinated efforts across network security, system administration, and incident response teams to create comprehensive defensive strategies that address both immediate vulnerabilities and long-term resilience requirements.
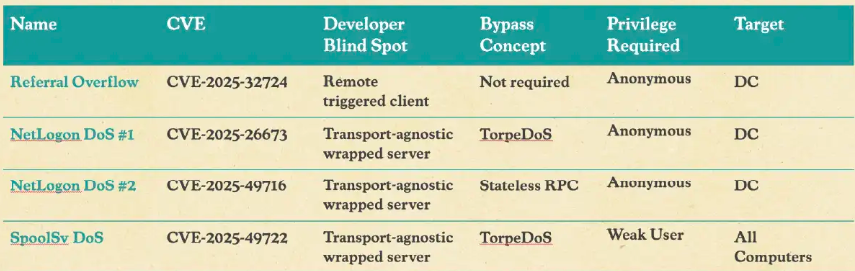
(Win-DDoS CVEs – Source: Safebreach)
 How CinchOps Can Help
How CinchOps Can Help
CinchOps understands that the Win-DDoS threat represents a fundamental shift in cybersecurity risk management, requiring sophisticated protective measures that many organizations struggle to implement independently.
Our comprehensive managed services approach addresses both the technical vulnerabilities and operational challenges that Win-DDoS attacks create for Houston businesses and beyond. We provide end-to-end protection that transforms complex cybersecurity challenges into manageable, cost-effective solutions that scale with your business needs.
- Rapid Vulnerability Assessment: Complete evaluation of domain controller configurations, internet exposure analysis, and patch status identification to assess immediate Win-DDoS risks across your entire Windows infrastructure environment.
- Emergency Patch Management: Accelerated deployment of Microsoft security updates addressing CVE-2025-26673, CVE-2025-32724, CVE-2025-49716, and CVE-2025-49722 with minimal operational disruption and comprehensive testing protocols.
- Network Security Architecture Review: Comprehensive analysis of current network security posture, including SD-WAN configurations, firewall rule optimization, and domain controller access control implementation for maximum protection.
- Advanced DDoS Protection Implementation: Deployment of enterprise-grade DDoS mitigation solutions, including cloud-based protection services and on-premises security appliances designed to handle massive Win-DDoS attack volumes.
- 24/7 Security Operations Center Services: Continuous monitoring and threat detection capabilities that identify Win-DDoS exploitation attempts and coordinate rapid incident response with minimal business impact.
- Managed IT Support Enhancement: Integration of Win-DDoS protection measures into existing managed IT support frameworks, ensuring comprehensive coverage without operational complexity or staff training requirements.
- Business Continuity Planning: Development of detailed incident response procedures and alternative operational methods to maintain critical business functions during sustained DDoS attacks.
- Customized Staff Training Programs: Comprehensive cybersecurity education that helps your team understand Win-DDoS threats and implement appropriate protective behaviors throughout your organization.
Our managed services provider approach ensures that Win-DDoS protection becomes an integrated component of your overall IT security strategy rather than an isolated point solution, providing Houston businesses with cost-effective protection that maintains operational flexibility in dynamic threat environments.
![]()
 Discover More
Discover More 
Discover more about our enterprise-grade and business protecting cybersecurity services: CinchOps Cybersecurity
Discover related topics: Critical Microsoft Exchange Server Vulnerability Threatens Houston Businesses Enabling Silent Cloud Compromise
For Additional Information on this topic: Win-DoS Epidemic: A Crash Course in Abusing RPC for Win-DoS & Win-DDoS
![]()
FREE CYBERSECURITY ASSESSMENT



