
Houston Business Ransomware Alert: Fileless Remcos RAT Attack Using PowerShell Evades Traditional Defenses
Invisible Threat: How Fileless Remcos RAT Bypasses Traditional Security – Practical Defenses Against Memory-Resident Malware
Houston Business Ransomware Alert: Fileless Remcos RAT Attack Using PowerShell Evades Traditional Defenses
Cybersecurity researchers have uncovered a new sophisticated attack campaign that uses a fileless version of Remcos RAT (Remote Access Trojan) to evade detection by traditional security solutions. This attack leverages PowerShell-based shellcode loading techniques and operates entirely in memory, leaving minimal evidence on disk.
 The Threat: Fileless Remcos RAT
The Threat: Fileless Remcos RAT
Remcos (Remote Control and Surveillance) RAT is a commercially available software tool that has been widely abused by threat actors for malicious purposes. The recently discovered variant (V6.0.0 Pro) comes with enhanced features that make it more dangerous than ever.
This remote access trojan operates as a fileless malware, running directly in the computer’s memory and bypassing traditional file-based detection methods. It uses sophisticated techniques to achieve persistence, steal sensitive data, and provide attackers with complete control over compromised systems.
 Severity of the Threat
Severity of the Threat
This threat represents a HIGH-SEVERITY risk for several reasons:
- It operates completely in memory, making it invisible to many traditional antivirus solutions
- It uses legitimate Windows tools (mshta.exe) for proxy execution, blending with normal system operations
- The attack employs multiple stages of obfuscation to hide its true purpose
- It establishes persistence through registry modifications
- Once installed, it provides attackers with comprehensive control including keylogging, webcam access, and data theft
 How It Works: The Infection Chain
How It Works: The Infection Chain
The attack chain begins when a user receives and opens a ZIP archive, often disguised with tax-related themes to entice victims. Here’s how the attack unfolds:
- A malicious Windows shortcut (LNK) file inside the ZIP archive is executed
- The LNK file uses mshta.exe (a legitimate Microsoft HTML Application host) to execute an obfuscated HTA file from a remote server
- The HTA file contains VBScript code that:
- Attempts to bypass Windows Defender by creating exclusion paths
- Downloads multiple payloads including a decoy PDF, another HTA file for persistence, and a PowerShell script
- Makes registry modifications to ensure automatic execution at startup
- The PowerShell script (24.ps1) is heavily obfuscated and contains code to:
- Decode and reconstruct a shellcode loader
- Allocate memory using VirtualAlloc()
- Copy the shellcode into memory using Marshal.Copy()
- Execute the code using CallWindowProcW()
- The shellcode loader dynamically resolves necessary API addresses by walking the Process Environment Block (PEB)
- Finally, the Remcos RAT payload is loaded and executed entirely in memory
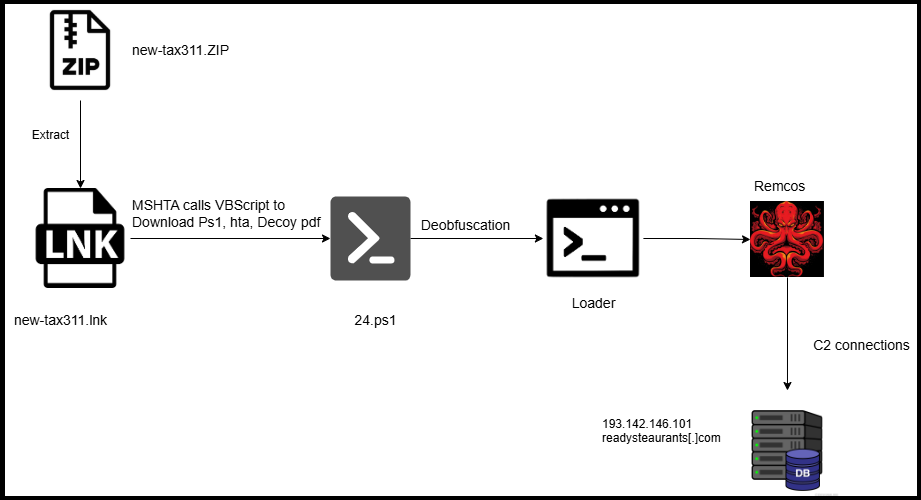
(Remcos RAT Attack Flow – Source: Qualys TRU)
 The Threat Actors
The Threat Actors
While the exact identity of the threat actors behind this campaign remains unknown, security researchers have noted that it bears similarities to previous Remcos RAT campaigns. Some reports suggest the loader component may be known as “K-Loader,” though this hasn’t been conclusively confirmed.
The sophistication of the attack indicates experienced malware operators who understand advanced evasion techniques and memory-based execution methods. The C&C server used in this campaign (readysteaurants[.]com) connects over TLS on port 2025, making the traffic difficult to detect.
 Who Is At Risk
Who Is At Risk
This attack campaign primarily targets:
- Small and medium-sized businesses with limited security resources
- Organizations relying heavily on traditional antivirus solutions without behavioral detection
- Users who may be susceptible to tax-related social engineering lures
- Companies without robust PowerShell logging and monitoring in place
- Systems without adequate endpoint detection and response capabilities
All industries should consider themselves potential targets, as the attackers appear to be opportunistic rather than focusing on specific sectors.
 Remediations and Protections
Remediations and Protections
To protect your organization from this sophisticated threat, implement these security measures:
- Enable PowerShell Logging: Configure comprehensive PowerShell logging (Script Block Logging, Module Logging, and Transcription) to detect suspicious scripting activity.
- Monitor MSHTA Usage: Flag unusual invocations of mshta.exe, especially when it attempts to access remote content.
- Watch for Registry Modifications: Monitor changes to Run keys in the Windows Registry that could indicate persistence mechanisms.
- Deploy Advanced EDR Solutions: Implement endpoint detection and response tools capable of detecting memory-only threats and suspicious API calls.
- Block LNK Files: Consider blocking or strictly controlling LNK file attachments through email gateways.
- User Training: Educate users about the dangers of opening unexpected attachments, even if they appear to relate to important topics like taxes.
- Enable AMSI Monitoring: Ensure Antimalware Scan Interface is active to help detect malicious scripts.
- Restrict PowerShell Execution: Implement AppLocker or similar controls to limit PowerShell execution to only authorized scenarios.
 How CinchOps Can Help
How CinchOps Can Help
At CinchOps, we understand the evolving threat of sophisticated fileless malware like this Remcos RAT variant. Our comprehensive managed IT services are specifically designed to protect small and medium-sized businesses from these advanced threats.
Our multi-layered approach to security includes:
- Advanced Endpoint Protection: Our solutions go beyond traditional antivirus, employing behavior-based detection to identify fileless malware operating in memory.
- 24/7 Security Monitoring: CinchOps continuously monitors your environment for suspicious activities, including unusual PowerShell executions and registry modifications.
- Email Security Gateway: We implement robust email filtering to block malicious attachments, including LNK files that could lead to Remcos infections.
- Security Awareness Training: We provide comprehensive training to your employees, helping them recognize and avoid social engineering attempts like tax-themed lures.
- Vulnerability Management: Our proactive approach ensures your systems are patched and configured to minimize exploitation opportunities.
Don’t let fileless threats like Remcos RAT put your business at risk. Contact CinchOps today for a comprehensive security assessment and learn how our managed IT support services can protect your organization from the latest cybersecurity threats.
![]()
 Discover More
Discover More 
Discover more about our enterprise-grade and business protecting cybersecurity services: CinchOps Cybersecurity
Discover related topics: The Rising Threat to Houston Businesses: How Business Email Compromise Fuels the 123% Surge in Ransomware Attacks
For Additional Information on this topic: Fileless Execution: PowerShell Based Shellcode Loader Executes Remcos RAT
![]()
FREE CYBERSECURITY ASSESSMENT



